Malicious scripts
- Dr. Afsaneh Javadi
- Jan 17, 2024
- 2 min read
People all over the world who work with technology use scripting and automation to make their tasks quicker and better. They often create sets of scripts using languages like PowerShell and Bash, which can carry out a series of instructions automatically. For instance, someone in charge might write a PowerShell script that runs whenever a new user joins a Windows domain. This script could set up their user account, manage access rights, send a welcome email, and do other administrative jobs. The script can be started by the administrator or linked to the human resources system to run automatically when a new employee is hired.
Unfortunately, this same technology that helps make work easier can also be used by people with bad intentions. Advanced Persistent Threat (APT) organizations, in particular, use scripts to automate parts of their harmful activities. For instance, they might use a PowerShell script whenever they get into a new Windows system to try different attacks to gain more privileges. Another script might run when they get administrative access to a system, connecting it to their control network, creating secret ways in for the future, and handling other routine tasks.
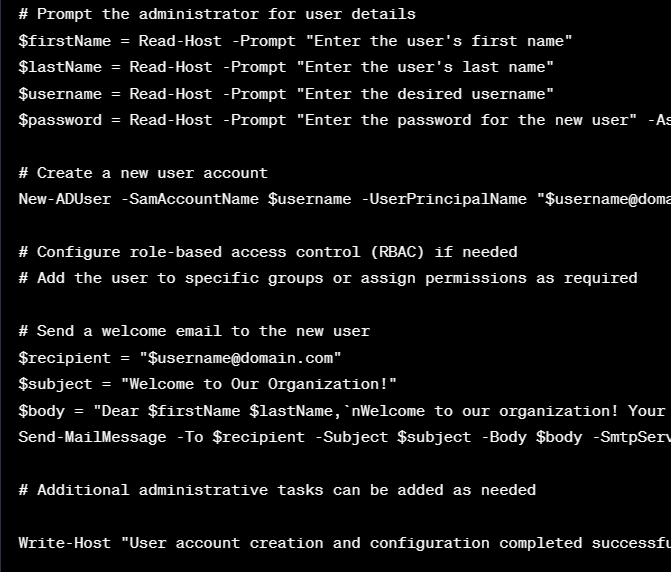
Below is a simple example of a non-malicious script using PowerShell. This script is designed to create and configure a new user account on a Windows domain:
Please note that this script is a basic example and may need adjustments based on your specific environment and requirements. Additionally, it uses PowerShell cmdlets related to Active Directory, so you need the appropriate permissions to execute these commands on an Active Directory domain controller.
Malicious scripts are also common in a type of malware called fileless malware. These attacks don't leave any files on the computer, making them harder to spot. For example, someone might get a harmful link in a fake email. Clicking the link could use a browser weakness to run a PowerShell script only in the computer's memory, causing a harmful action. Since nothing is written to the computer's storage, security systems that depend on finding saved files might not catch the attack.

コメント